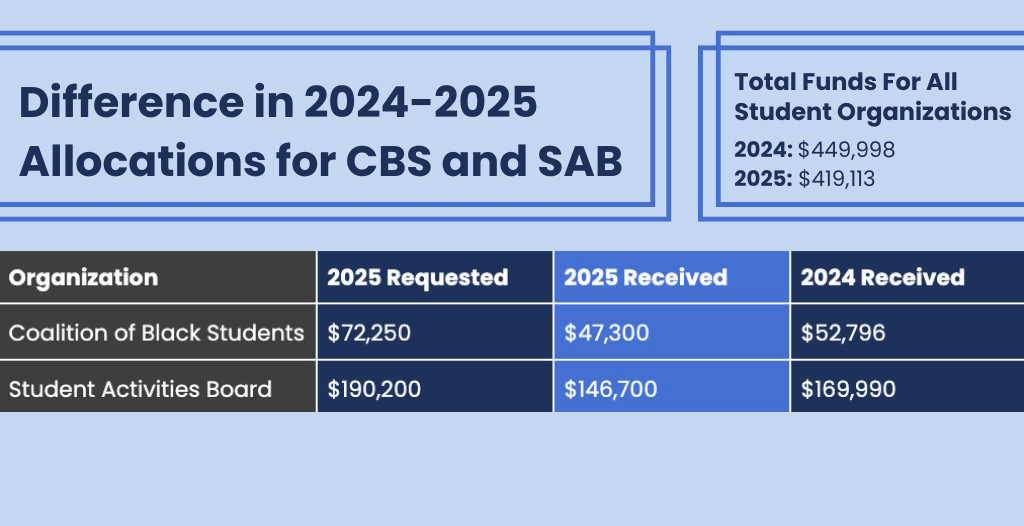
Before the 2022 spring semester, Drake Information Technology Services (ITS) will be implementing new multi-factor authorization to log into Drake accounts to better protect Drake from cyberattacks.
“Multi-factor authentication is the best tool we have to prevent accounts and data from being compromised,” Chief Information Technology Officer Keren Fiorenza said via email. “Drake receives over 5 million emails in an average month and 60-70 percent of those are phishing, spam, or other malicious emails. Each day there are thousands of attempts to hack Drake accounts. Most of those attempts can be stopped by requiring a second method of identity verification. ITS is putting this system in place because that additional authentication protects all of us.”
The rollout of multi-factor authentication will be staggered starting Jan. 4, according to Technical Project Manager Jeff Regan. The first platforms to require multi-factor authentication will be eAccounts and Self-Service Banner, followed by TouchNet and Blackboard, then the Microsoft 365 suite. The process will finish with employee-only items, and student employees will have to start using multi-factor authentication to access their timecards.
“The idea behind [multi-factor authentication] is essentially a way to verify who you are when you’re logging into a system,” ITS Communications Manager Carla Herling said. “So typically you take something you know—that is, your login, in our case your Drake email address and password, and something you have, and we’re promoting the use of a Microsoft Authenticator App that you use on your cell phone. And so you have, in addition to logging in, you have an additional verification step that proves who you are, so there’s an extra level of security for the system.”
According to Regan, students will download the Microsoft Authenticator app or alternatively use a text or automated phone call for multi-factor authentication. Regan said the application has been very effective in the past at stopping cyberattacks because it is more difficult for hackers to get through.
“There’s never a great time to make a big shift, unfortunately, and this will be definitely a tough time for those who are in J-Term, and we understand that, so we’re trying to reach out to those faculty and students directly so that they understand that that change is coming and help them prepare,” Regan said.
Previously, Herling said, faculty and staff used multi-factor authentication on a different system. After the student rollout, they will be switched over to the Microsoft Authenticator tool as well.
“Currently, we have a platform that we use for faculty and staff, and we’ve had that going for several years now,” Herling said. “It’s something that has always been the plan to expand to students, and as we have been using the Microsoft platform more and more, we’ve been kind of watching the Microsoft Authenticator tool.”
According to Herling, ITS already has multiple strategies in place to protect against cyberattacks, including email labeling from non-Drake email addresses. However, ITS hopes multi-factor authentication will provide an extra layer of security.
A recent cyberattack at DMACC also increased the incentive for multi-factor authentication and showed ITS they were on the right path, Regan said. According to the virus protection company Emsisoft, there were at least 26 ransomware attacks involving U.S. universities and colleges in 2020.
“Part of the reason behind the switch now is that, especially over the pandemic, but really, frankly, over the last 8-10 years, cyber attacks have been growing exponentially and colleges and universities have really become a key target for those cyber criminals,” Herling said.
ITS is currently offering $1 off coupons to Starbucks for the first 150 users who sign up early for multi-factor authentication. According to Regan, it will be easier for students to sign up before the change happens, and those who wait until after will have to go through extra steps.
“We’re really encouraging faculty, staff, and students to go through the links that [were sent] and the instruction documents that have come out on campus and register in the authenticator app, if they are going to use the mobile phone application, or just set up their other methods if they want to use a call or text message before January, before the end of the year,” Regan said.
To learn how to add multi-factor authentication to your Drake accounts, visit https://drake.teamdynamix.com/TDClient/2025/Portal/KB/?CategoryID=3964.